奇淫技巧
已知dp,dq,c,n,p,q
理论证明
我们知道
所以存在一个值k,使得下式成立
将上述式子分别模p,q,得到
由上述可知,我们可以令
将(5)带入到(4)中,得到
由于gcd(p,q)=1,所以我们得到k值得同余式:
将(7)带入到(5)中,得到
将(8)带入到(1)中,
对于mp以及mq,求法如下:
由费马小定理可知
所以,
这样就万事俱备!!
一般实现代码如下:
1 | #!usr/env/python3 |
已知dp,e,c,n
理论证明
我们可以知道
之后我们可以知道:
将dp*e之后
所以e*dp-1是p-1的k倍,k在(1,e)之中(原因是dp在p-1之内)
下面就就写一下关于爆破e值的脚本,从而求出d
1 | #!usr/env/python3 |
题目
rsa(2019/11/11湖湘杯初赛)
1 |
已知dp,dq
dp = d mod (p-1)
dq = d mod (q-1)
已知p+q与pq
根据题目要求可以求出pq与p+q,这时候可以直接求出fn
题目
rsa
Do you know what e is it?
打开文件,有两个文件,一个python文件,一个output
1 | #output |
1 | #output |
分析:利用123对应的那个密文,解出e值,
利用上面的式子,我们可以利用上述的式子
求出p+q后,就可以顺手解出fn
1 | #!usr/env/python3 |
分解模数N
方法介绍
n比较小的话,可以手写脚本进行爆破1
2
3
4
5
6
7#coding=utf-8
for i in range(2,n):
if(n%i == 0):
p = i
q = n/i
breakn比较大的话,可以使用一些攻击进行暴力破解,如RSATool或者yafu一个在线分解大素数的网站:
http://factordb.com,这个网站只能分解已经存在分解过的模数n值
题目
xyf(Jarvisoj)
1 | n=3161262255255421133292506694323988711204792818702640666084331634444148712428915950639954540974469931426618702044672318134908678730641981414037034058320359158246813987154679178159391832232990193738454116371045928434239936027006539348488316754611586659587677659791620481200732564068367148541242426533823626586574915275209508300120574819113851895932912208783915652764568319771482309338434364094681579135086703127977870534715039005822312878739611630155714313119545610939253355808742646891815442758660278514976431521933763272615653261044607041876212998883732724662410197038419721773290601109065965674129599626151139566369 |
使用yafu对模数进行分解:
1 | p= 56225103425920179745019828423382255030086226600783237398582720244250840205090747144995470046432814267877822949968612053620215667790366338413979256357713975498764498045710766375614107934719809398451422359883451257033337168560937824719275885709824193760523306327217910106187213556299122895037021898556005848927 |
脚本:
1 | #coding=utf-8 |
Factoring with High Bits Known
当我们知道一个公钥中模数N的一个因子的较高位时,我们就有一定几率来分解N。
需要安装sage
下载好之后,进行如下操作:
1 | $ tar xvf sage-8.9-Ubuntu_18.04-x86_64.tar.bz2 |
模板:
1 | from sage.all import * |
题目
cry
给了个cry.py文件和访问链接:
nc pwn2.jarvisoj.com 9891
看完代码:
- 先随机生成了一个模数n以及e,需要使用n与e对任一一个信息进行加密,然后转成hex形式,传入程序才能走向下一步
- 之后给出了使用base64加密的密文,以及使用RSA加密的aes_key和初始向量IV
- AES是一种对称加密,也就是加密密钥和解密密钥是相同的
1 | nc pwn2.jarvisoj.com 9891 |
通过得到的n,e任一加密一段字符串
1 | #!/usr/bin/python |
通过交互页面得到密文c以及aes_key和iv,这里只给出p的高位,所以需要我们进行爆破,求出最终的p来,下面是ans.sage文件:
1 | #coding=utf-8 |
剩下就可以直接开始解密了:
1 | #coding=utf-8 |
Rabin算法
hardRSA——Jarvis OJ
加压后发现两个文件,一个公钥,一个enc文件
使用openssl查看
1 | openssl rsa -in pubkey.pem -pubin -text -modulus |
典型的rabin加密,使用模块叫脚本即可:
1 | #coding=utf-8 |
一句话加密
下载附件得到两个文件,一个图片,一个encode.py
1 | #encode.py |
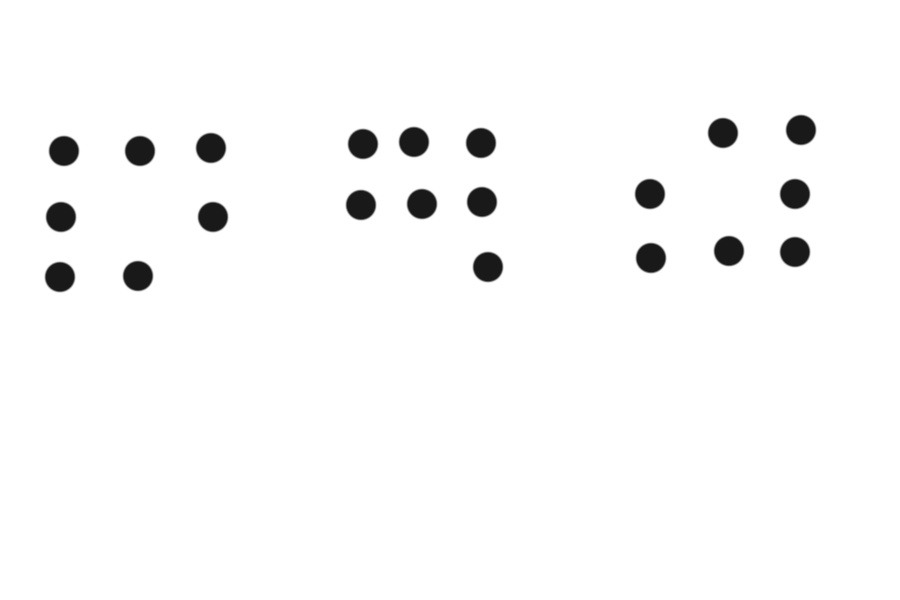
使用winhex打开查看它,发现末尾有一段
0xc2636ae5c3d8e43ffb97ab09028f1aac6c0bf6cd3d70ebca281bffe97fbe30dd?kobe"
本来以为图片是e.png,所以这是e的值,但发现可以使用yafu将其分解成两个大素数,所以认为这个是模数n
这里还有一个提示信息,就是kobe,图片上的符号表示的是kobecode,还是见识太少
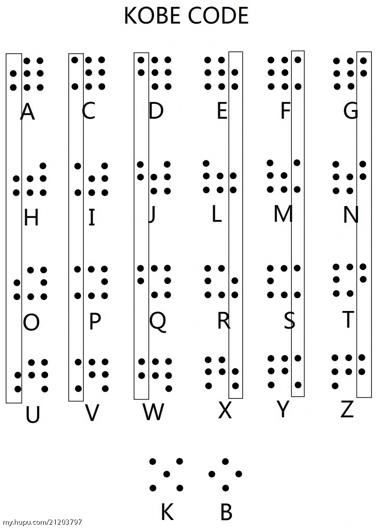
翻译出来是TWO,所以猜测是rabin加密,解密如下:
1 | #coding=utf-8 |
共模攻击(Common Modulus Attack)
使用相同的模数n,但是使用了不同的公钥e加密同一明文信息,且公钥中
e1,e2应该互质。
方法
结论:当n不变的情况下,知道
n,e1,e2,c1,c2可以在不知道d1,d2情况下,解出m。
证明
由RSA基本原理可知:
由于e1与e2互质,由贝祖等式可知,必有s1,s2满足:
s1,s2皆为整数,但是一正一负,我们可以通过扩展欧几里得算法计算s1,s2
所以:
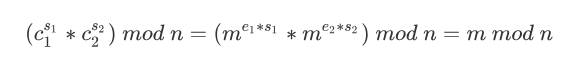
题目积累
very hard RSA(JarvisoJ)
解压下来有三个文件,两个enc文件,和一个加密的python脚本
1 | #veryhrdrsa.py |
通过算法很容易知道是共模攻击,所以我们不需要的得到密钥d就可以进行解密:
这里出现了一个问题,就是使用gmpy无法进行解密,可能是我脚本写的有问题,目前没有找到解决方案。
1 | import gmpy2 |
rsappend(jarvisoJ)
解压下来有两个文件,一个python脚本程序,一个可读文本
1 | flag = open("flag", "r").read().strip() |
直接看看关键位置,发现使用不同的e对密文进行了32次加密,但是模数n是相同的,所以这里是共模攻击
第一行数是模数n值,之后每个对应一个密文,只需要两个就可以直接解密
1 | #coding=utf-8 |
xgm(Jarvisoj)
下载下来有一个txt文件
1 | n1=21660190931013270559487983141966347279666044468572000325628282578595119101840917794617733535995976710097702806131277006786522442555607842485975616689297559583352413160087163656851019769465637856967511819803473940154712516380580146620018921406354668604523723340895843009899397618067679200188650754096242296166060735958270930743173912010852467114047301529983496669250671342730804149428700280401481421735184899965468191802844285699985370238528163505674350380528600143880619512293622576854525700785474101747293316814980311297382429844950643977825771268757304088259531258222093667847468898823367251824316888563269155865061 |
一个简单的共模攻击
1 | #coding=utf-8 |
低加密指数攻击
基本理论
选择小的
e可以缩短加密时间,但是选择的e不当,可能会造成严重的安全问题。在CTF题型中,这种攻击一般适用于e=3,
明文过小,导致明文的三次方还是小于n
1
2
3#此时只需要对密文开三次方即可
import gmpy2
gmpy2.iroot(c,e)如果m稍微大一点,那么
我们可以对k进行枚举
1 | import gmpy2 |
题目积累
Extremely hard RSA(jarvisoj)
解压后发现两个文件,一个密文文件,一个公钥文件,同样使用openssl命令查看公钥信息
1 | root@DESKTOP-OORTB87:/mnt/c/Users/X1TABLET/Desktop/RSA/extremelyhardRSA# openssl rsa -in pubkey.pem -pubin -text -modulus |
下面直接写脚本解密:
ps:gmpy中求根号是gmpy.root gmpy2中求根号是gmpy2.iroot
1 | #coding=utf-8 |
xbk(Jarvisoj)
1 | n=47966708183289639962501363163761864399454241691014467172805658518368423135168025285144721028476297179341434450931955275325060173656301959484440112740411109153032840150659 |
解密脚本:
1 | #coding=utf-8 |
选择密文攻击
题目记录
打开链接看到三个选项,很明显可以使用选择密文攻击
- 首先要让其r < n,r = 2,加密值如下,记为x, :
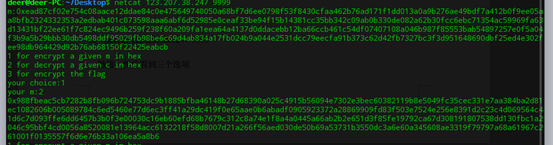
然后读出flag的密文值,记为c, :
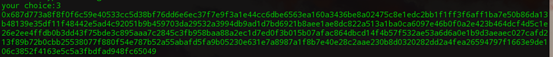
将flag的密文与m的密文相乘,然后模n,得到y, ,又因为
chice2是有解密的,所以将y解密得到下面一行,记为u,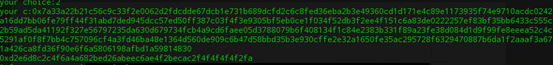
由
RSA原理可知m = u//r#这里的//代表整除
大致脚本如下
1
2
3
4
5#coding:utf-8
from Crypto.Util import number
data = 0xd2e6d8c2c4f6a4a682bed26abeec6ae4f2becac2f4f4f4f4f2fa//2 #整除
m = number.long_to_bytes(data)
print(m)得到
flag: islab{RSA_i5_v5ry_eazzzzy}
私钥恢复和最优非对称加密填充
基本理论
题目积累
GOD LIKE RSA(jarvisoj)
解压之后,有三个文件,一个公钥文件,一个密文文件,一个损坏的私钥文件
查看公钥信息:
1 | RSA Public-Key: (4096 bit) Modulus: 00:c0:97:78:53:45:64:84:7d:8c:c4:b4:20:e9:33: 58:67:ec:78:3e:6c:f5:f0:5c:a0:3e:ee:dc:25:63: d0:eb:2a:9e:ba:8f:19:52:a2:67:0b:e7:6e:b2:34: b8:6d:50:76:e0:6a:d1:03:cf:77:33:d8:b1:e9:d7: 3b:e5:eb:1c:65:0c:25:96:fd:96:20:b9:7a:de:1d: bf:fd:f2:b6:bf:81:3e:3e:47:44:43:98:bf:65:2f: 67:7e:27:75:f9:56:47:ba:c4:f0:4e:67:2b:da:e0: 1a:77:14:40:29:c1:a8:67:5a:8f:f5:2e:be:8e:82: 31:3d:43:26:d4:97:86:29:15:14:a9:69:36:2c:76: ed:b5:90:eb:ec:6f:ce:d5:ca:24:1c:aa:f6:63:f8: 06:a2:62:cb:26:74:d3:5b:82:4b:b6:d5:e0:49:32: 7b:62:f8:05:c4:f7:0e:86:59:9b:f3:17:25:02:aa: 3c:97:78:84:7b:16:fd:1a:f5:67:cf:03:17:97:d0: c6:69:85:f0:8d:fa:ce:ee:68:24:63:06:24:e1:e4: 4c:f8:e9:ad:25:c7:e0:c0:15:bb:b4:67:48:90:03: 9b:20:7f:0c:17:eb:9d:13:44:ab:ab:08:a5:c3:dc: c1:98:88:c5:ce:4f:5a:87:9b:0b:bf:bd:d7:0e:a9: 09:59:81:fa:88:4f:59:60:6b:84:84:ad:d9:c7:25: 8c:e8:c0:e8:f7:26:9e:37:95:7c:e1:48:29:0f:51: e7:bd:98:2f:f6:cc:80:e7:f0:32:0b:89:51:92:4e: c2:6d:50:53:2b:3b:77:72:d1:bd:1a:1f:92:d7:12: 79:61:61:c5:a4:7e:b3:85:eb:f0:7c:6d:46:03:c5: e6:d5:81:2c:ba:7e:ea:8d:51:7d:63:55:34:2a:b6: d4:dc:31:5a:f1:99:e3:dc:8c:83:0b:a2:2a:d5:3c: 41:48:41:54:1a:a9:e8:b6:70:bf:d3:fe:ed:19:17: 14:94:13:b3:17:e3:8b:8e:6f:53:ed:e2:44:e8:4a: 32:d6:5c:0d:a8:80:f5:fc:02:e9:46:55:d5:a4:d3: e7:c6:30:77:f9:73:e9:44:52:d8:13:9d:5d:bf:9e: fa:3a:b5:96:79:82:5b:cd:19:5c:06:a9:00:96:fd: 4c:a4:73:88:1a:ec:3c:11:de:b9:3d:e0:50:00:1e: ac:21:97:a1:96:7d:6b:15:f9:6c:c9:34:7f:70:d7: 9d:2d:d1:48:4a:81:71:f8:12:dd:32:ba:64:31:60: 08:26:4b:09:22:03:83:90:17:7f:f3:a7:72:57:bf: 89:6d:e4:d7:40:24:8b:7b:bd:df:33:c0:ff:30:2e: e8:6c:1d Exponent: 65537 (0x10001) Modulus=C09778534564847D8CC4B420E9335867EC783E6CF5F05CA03EEEDC2563D0EB2A9EBA8F1952A2670BE76EB234B86D5076E06AD103CF7733D8B1E9D73BE5EB1C650C2596FD9620B97ADE1DBFFDF2B6BF813E3E47444398BF652F677E2775F95647BAC4F04E672BDAE01A77144029C1A8675A8FF52EBE8E82313D4326D49786291514A969362C76EDB590EBEC6FCED5CA241CAAF663F806A262CB2674D35B824BB6D5E049327B62F805C4F70E86599BF3172502AA3C9778847B16FD1AF567CF031797D0C66985F08DFACEEE6824630624E1E44CF8E9AD25C7E0C015BBB4674890039B207F0C17EB9D1344ABAB08A5C3DCC19888C5CE4F5A879B0BBFBDD70EA9095981FA884F59606B8484ADD9C7258CE8C0E8F7269E37957CE148290F51E7BD982FF6CC80E7F0320B8951924EC26D50532B3B7772D1BD1A1F92D712796161C5A47EB385EBF07C6D4603C5E6D5812CBA7EEA8D517D6355342AB6D4DC315AF199E3DC8C830BA22AD53C414841541AA9E8B670BFD3FEED1917149413B317E38B8E6F53EDE244E84A32D65C0DA880F5FC02E94655D5A4D3E7C63077F973E94452D8139D5DBF9EFA3AB59679825BCD195C06A90096FD4CA473881AEC3C11DEB93DE050001EAC2197A1967D6B15F96CC9347F70D79D2DD1484A8171F812DD32BA64316008264B0922038390177FF3A77257BF896DE4D740248B7BBDDF33C0FF302EE86C1D writing RSA key -----BEGIN PUBLIC KEY----- MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAwJd4U0VkhH2MxLQg6TNY Z+x4Pmz18FygPu7cJWPQ6yqeuo8ZUqJnC+dusjS4bVB24GrRA893M9ix6dc75esc ZQwllv2WILl63h2//fK2v4E+PkdEQ5i/ZS9nfid1+VZHusTwTmcr2uAadxRAKcGo Z1qP9S6+joIxPUMm1JeGKRUUqWk2LHbttZDr7G/O1cokHKr2Y/gGomLLJnTTW4JL ttXgSTJ7YvgFxPcOhlmb8xclAqo8l3iEexb9GvVnzwMXl9DGaYXwjfrO7mgkYwYk 4eRM+OmtJcfgwBW7tGdIkAObIH8MF+udE0Srqwilw9zBmIjFzk9ah5sLv73XDqkJ WYH6iE9ZYGuEhK3ZxyWM6MDo9yaeN5V84UgpD1HnvZgv9syA5/AyC4lRkk7CbVBT Kzt3ctG9Gh+S1xJ5YWHFpH6zhevwfG1GA8Xm1YEsun7qjVF9Y1U0KrbU3DFa8Znj 3IyDC6Iq1TxBSEFUGqnotnC/0/7tGRcUlBOzF+OLjm9T7eJE6Eoy1lwNqID1/ALp RlXVpNPnxjB3+XPpRFLYE51dv576OrWWeYJbzRlcBqkAlv1MpHOIGuw8Ed65PeBQ AB6sIZehln1rFflsyTR/cNedLdFISoFx+BLdMrpkMWAIJksJIgODkBd/86dyV7+J beTXQCSLe73fM8D/MC7obB0CAwEAAQ== -----END PUBLIC KEY----- |
模数n有4096bit,分解不太现实,所以目前还是使用损坏的私钥文件,修复脚本(具体也能在基本理论的链接中找到)
1 | #!/usr/bin/python3 |
然后使用openssl进行解密,此处加密填充方式使用的是OAEP padding方式,所以解密时应该注意:
1 | openssl rsautl -decrypt -inkey private.pem -keyform PEM -in flag.enc -oaep |
或者写脚本:
1 | # coding=utf-8 |
Openssl使用
openssl命令
查看公钥pem信息
1
openssl rsa -in pubkey.pem -pubin -text -modulus
利用生成私钥解密
1
openssl rsautl -decrypt -inkey pkey -in flag.enc -out out.txt
生成私钥
1
openssl asn1parse -genconf [config file] -out newkey.der
Medium RSA——Jarvis OJ
方法一
解压后发现了两个文件,一个.pem文件,一个.enc文件
1 | RSA Public-Key: (256 bit) Modulus: |
使用yafu对模数进行分解得到
1 | p = 275127860351348928173285174381581152299 |
解密脚本:
1 | #coding=utf-8 |
方法二
使用RSAtools或者脚本生成密钥文件,使用openssl解密,
私钥生成脚本:
1 | #coding=utf-8 |
使用
1 | openssl rsautl -decrypt -inkey private.pem -in flag.enc -out out.txt |
得到PCTF{256b_i5_m3dium}